A new vulnerability was discovered in All in One SEO Pack. The newly discovered exploit allows attackers to take full control of a website using a cross site scripting attack.
Cross Site Scripting Vulnerability
Researchers discovered a type of issue that is called a cross site scripting vulnerability (XSS).
It can generally involve a compromised input interface. So anywhere that a user can input and upload content, images or scripts needs to be “sanitized” in order to prevent malicious scripts from being uploaded.
Typical entry points can be comments and forms. But these kinds of exploits can also affect areas of the site that are walled off from non-registered users.
The vulnerability affecting All in One SEO Pack affects an area of the site that requires a user to have posting privileges.
Because of this, it’s characterized as a medium level vulnerability.
Is All in One SEO Pack Vulnerable?
Yes, All in One SEO Pack (versions 3.6.1 and under) is vulnerable to an XSS exploit.
This particular exploit affects an input area that is not sanitized.
The affected area is the SEO title and SEO description fields, where a logged in user with posting privileges can upload malicious scripts to gain administrative access, take over the site, or to infect site visitors.
As bad as that sounds, this is a medium level severity vulnerability because it requires a hacker to access log-in credentials of a registered user with posting privileges.
In order to accomplish that the hacker might need to employ social engineering tricks to steal the credentials or take advantage of a vulnerability in another plugin or theme.
According to WordFence, this is how the vulnerability could wreak havoc:
“Due to the JavaScript being executed whenever a user accessed the ‘all posts’ page, this vulnerability would be a prime target for attackers that are able to gain access to an account that allows them to post content.
Since Contributors must submit all posts for review by an Administrator or Editor, a malicious Contributor could be confident that a higher privileged user would access the ‘all posts’ area to review any pending posts.
If the malicious JavaScript was executed in an Administrator’s browser, it could be used to inject backdoors or add new administrative users and take over a site.”
How Vulnerability Was Discovered
Security researchers at WordFence discovered the vulnerability in All in One SEO Pack on July 10, 2020 and immediately notified the publishers of the plugin.
The publishers set to work on updating the vulnerability and released a patch on July 15, 2020, five days later.
Premium users of the WordFence Security Plugin received a firewall rule update on the same day that the vulnerability was discovered, July 10, 2020.
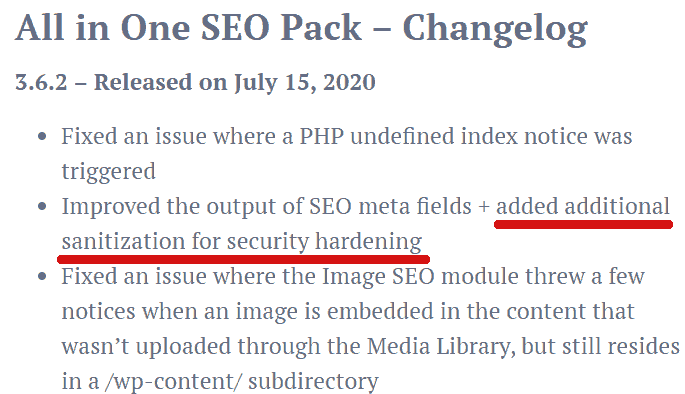
The update to All in One SEO Pack is correctly referred to in their changelog:
“Improved the output of SEO meta fields + added additional sanitization for security hardening”
Screenshot of All in One SEO Pack Changelog
Update All in One SEO Pack to 3.6.2
Everyone who uses All in One SEO Pack is encouraged to update their plugin to version 3.6.2 immediately. While this is rated as a medium severity vulnerability it is still prudent to patch the plugin so that it is safe.
Citation
Read the official WordFence Announcement
2 Million Users Affected by Vulnerability in All in One SEO Pack