The U.S. Government National Vulnerability Database (NVD) published notice of a critical vulnerability affecting the Forminator WordPress Contact Form plugin up to an including version 1.24.6.
Unauthenticated attackers can upload malicious files to websites which, according to the warning, “may make remote code execution possible.”
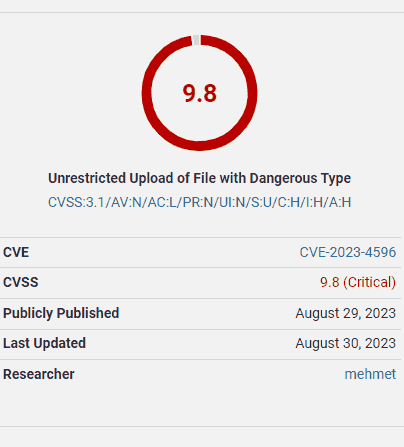
The vulnerability score rating is 9.8, on a scale of one to ten, with ten being the most severe vulnerability level.
Screenshot Of Wordfence Advisory
 Screenshot from Wordfence.com
Screenshot from Wordfence.comVulnerability To Unauthenticated Attackers
Many vulnerabilities tend to require an attacker to first attain a WordPress user level before they can launch an attack.
For example, some vulnerabilities are available to those with a subscriber user level, others require contributor or admin level in order to perform an attack.
What makes this vulnerability particularly worrisome is that it allows unauthenticated attackers, those with no user level at all, to successfully hack the site.
A second reason why this vulnerability is rated 9.8 on a scale of 1 – 10 (critical) is that the attacker can upload an arbitrary file, which means any kind of file, like a malicious script.
The National Vulnerability Database (NVD) describes the vulnerability:
“The Forminator plugin for WordPress is vulnerable to arbitrary file uploads due to file type validation occurring after a file has been uploaded to the server in the upload_post_image() function in versions up to, and including, 1.24.6.
This makes it possible for unauthenticated attackers to upload arbitrary files on the affected site’s server which may make remote code execution possible.”
Remote Code Execution
A Remote Code Execution (RCE) vulnerability is a type of exploit where the attacker can execute malicious code on the attacked website remotely from another machine.
The damage from this kind of exploit can be as severe as a full site takeover.
Contact Forms Must Be Locked Down
WordPress plugins that allow a registered or unauthenticated users to upload anything, even text or images, must have a way to limit what can be uploaded.
Contact Forms must be especially locked down because they accept input from the public.
RCE Not Specific To WordPress
These kinds of vulnerabilities are not particular to WordPress, they can happen to any Content Management System.
WordPress publishes coding standards for publishers to know how to prevent these kinds of things.
The WordPress developer page for plugin security (Sanitizing Data) explains how to properly handle uploads from untrusted sources.
The developer page advises:
“Untrusted data comes from many sources (users, third party sites, even your own database!) and all of it needs to be checked before it’s used.
Sanitizing input is the process of securing/cleaning/filtering input data.
Validation is preferred over sanitization because validation is more specific.
But when “more specific” isn’t possible, sanitization is the next best thing.”
Has the Forminator Contact Form Plugin Fixed The Vulnerability?
According to National Vulnerability Database and the Wordfence WordPress security company, the issue has been addressed in version 1.25.0.
Wordfence recommends updating to the latest version:
“Update to version 1.25.0, or a newer patched version…”
Forminator Plugin Changelog
A changelog is a record of all the changes made to a software. It allows users to read it and determine whether or not they want to update their software.
It’s a good practice to let your users know that a software update contains a fix (called a patch) for a vulnerability.
This lets users know that a particular update is urgent so that they can make an informed decision about updating their software.
Otherwise, how would a software user know that an update is urgent without the changelog informing them, right?
Judge for yourself whether the Forminator changelog offers sufficient notification to their users about a vulnerability patch:
Screenshot of Forminator Changelog

Sources:
Read the official National Vulnerability Database advisory:
Read the Wordfence advisory on the Forminator WordPress Contact Form Plugin Vulnerability
Forminator <= 1.24.6 – Unauthenticated Arbitrary File Upload
Read the Exploit Database report on the Forminator Contact Form vulnerability
WordPress Plugin Forminator 1.24.6 – Unauthenticated Remote Command Execution
Featured image by Shutterstock/ViDI Studio





