High severity vulnerability was discovered in the Elementor website builder plugin that could allow an attacker to upload files to the website server and execute them. The vulnerability is in the template uploader functionality.
Elementor Unrestricted Upload of File with Dangerous Type Vulnerability
Elementor website builder is a popular WordPress plugin with over 5 million installations. The popularity is driven by its simple to use drag and drop functionality for creating professional looking websites.
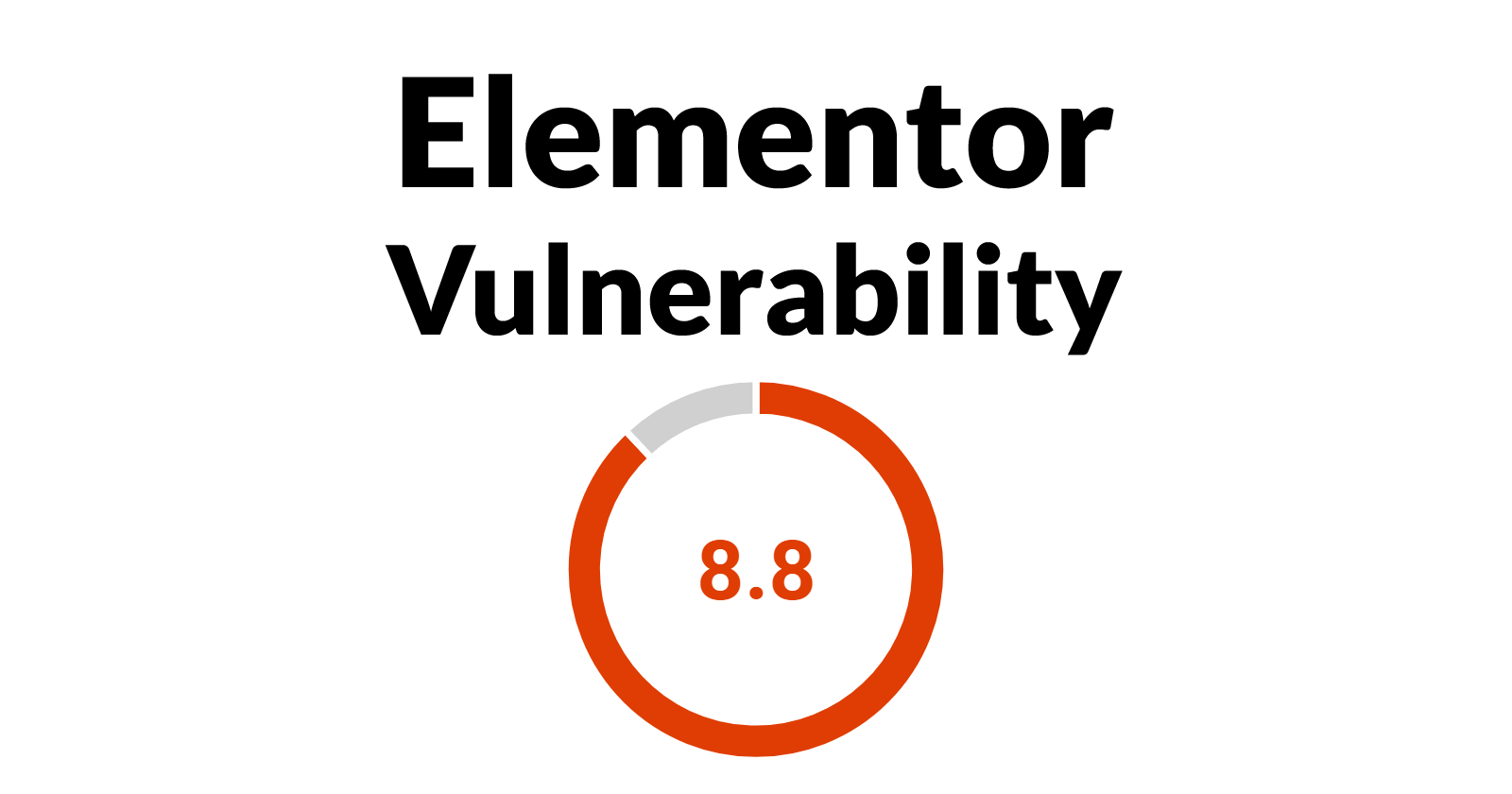
The vulnerability discovered in Elementor is rated 8.8/10 and is said to make websites using Elementor open to a Remote Code Execution whereby an attacker is able to essentially control the affected website and run various commands.
The type of vulnerability is described as an Unrestricted Upload of File with Dangerous Type. This kind of vulnerability is an exploit where an attacker is able to upload malicious files which in turn enables the attacker to execute commands on the affected website server.
This kind of issue is generally described in this manner:
“The product allows the attacker to upload or transfer files of dangerous types that can be automatically processed within the product’s environment.”
Wordfence describes this specific vulnerability:
“The Elementor Website Builder …plugin for WordPress is vulnerable to Remote Code Execution via file upload in all versions up to and including 3.18.0 via the template import functionality.
This makes it possible for authenticated attackers, with contributor-level access and above, to upload files and execute code on the server.”
Wordfence also indicates that there is no patch to fix this issue and recommends uninstalling Elementor.
“No known patch available. Please review the vulnerability’s details in depth and employ mitigations based on your organization’s risk tolerance. It may be best to uninstall the affected software and find a replacement.”
Elementor 3.18.1 Version Update
Elementor released an update to version 3.18.1 today. It is unclear if this patch fixes the vulnerability as the Wordfence site currently states that the vulnerability is unpatched.
The changelog describes this update:
“Fix: Improved code security enforcement in File Upload mechanism”
This is a newly reported vulnerability and the facts may change. Wordfence however warns that hackers are already attacking Elementor websites because their paid version has already blocked eleven hacking attempts at the time of publishing the announcement.
Read the Wordfence advisory: