A WordPress vulnerability rated as critical has been patched. Although the exploit is labeled as critical, one security researcher states that the likelihood of the vulnerability being exploited is remote.
The patch is applied to WordPress version 5.7.2. Sites opted into automatic download should be receiving this update without any additional action by publishers.
Publishers are encouraged to check what WordPress version they are using to make sure they are updated to version 5.7.2.
Object Injection Vulnerability
The vulnerability that is affecting WordPress is called an Object Injection vulnerability. Specifically, it is an object injection in PHPMailer vulnerability.
According to the Owasp.org security website, this is the definition of a PHP Object Injection vulnerability:
“PHP Object Injection is an application level vulnerability that could allow an attacker to perform different kinds of malicious attacks, such as Code Injection, SQL Injection, Path Traversal and Application Denial of Service, depending on the context.
The vulnerability occurs when user-supplied input is not properly sanitized before being passed to the unserialize() PHP function.
Since PHP allows object serialization, attackers could pass ad-hoc serialized strings to a vulnerable unserialize() call, resulting in an arbitrary PHP object(s) injection into the application scope.”
WordPress Vulnerability Rated as Critical
The vulnerability is rated at near the highest rating level of criticality. On a scale of 1 to 10 using the Common Vulnerability Scoring System (CVSS), this vulnerability is rated at 9.8.
The Patchstack security website published the official United States government vulnerability rating.
WordPress Vulnerability Rated Critical
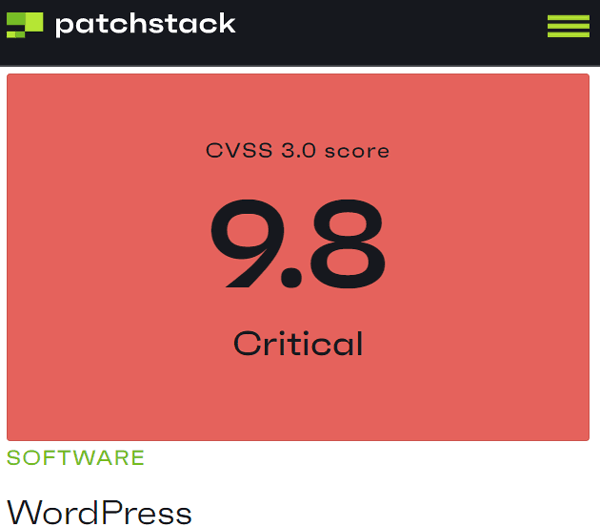 WordPress vulnerability is rated 9.8 on a scale of 1 – 10.
WordPress vulnerability is rated 9.8 on a scale of 1 – 10.According to the Patchstack security site that published details of the vulnerability:
“Details
Object injection in PHPMailer vulnerability discovered in WordPress (one security issue affecting WordPress versions between 3.7 and 5.7).
SOLUTION
Update the WordPress to the latest available version (at least 5.7.2). All WordPress versions since 3.7 have also been updated to fix the following security issue.”
The official WordPress announcement for WordPress 5.7.2 stated:
“Security updates
One security issue affects WordPress versions between 3.7 and 5.7.If you haven’t yet updated to 5.7, all WordPress versions since 3.7 have also been updated to fix the following security issues:
Object injection in PHPMailer”
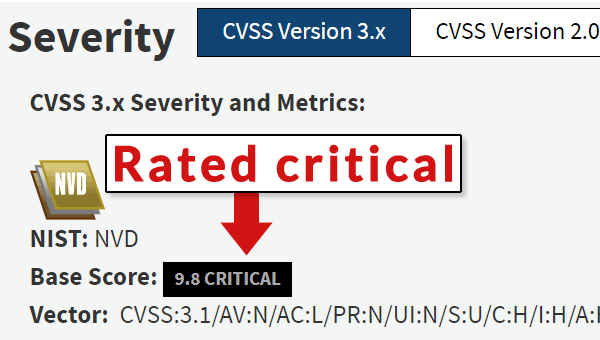
The official United States government National Vulnerability Database website that announces vulnerabilities noted that this problem happened because a fix for a previous vulnerability created a new one.
The U.S Government National Vulnerability Database describes the vulnerability like this:
“PHPMailer 6.1.8 through 6.4.0 allows object injection through Phar Deserialization via addAttachment with a UNC pathname.
NOTE: this is similar to CVE-2018-19296, but arose because 6.1.8 fixed a functionality problem in which UNC pathnames were always considered unreadable by PHPMailer, even in safe contexts.
As an unintended side effect, this fix eliminated the code that blocked addAttachment exploitation.”
National Vulnerability Database Rates WordPress Vulnerability as Critical
WordFence Says No Need to Panic
The security researchers at Wordfence stated that there’s no need to panic. In their expert opinion, Wordfence downplayed the likelihood of an exploit happening because of this vulnerability.
“In our assessment, successfully exploiting this vulnerability would require a large number of factors to line up, including the presence of at least one additional vulnerability in a plugin or other component installed on the site as well as the presence of a vulnerable magic method.
We are also currently unaware of any plugins that could be used to exploit this vulnerability even as a site administrator.
This is unlikely to be used as an intrusion vector, though it is possible that it could be used by attackers who have already gained some level of access to escalate their privileges.”
Update WordPress Immediately
Publishers who use WordPress should consider checking if their WordPress installations are the latest. The most current version of WordPress is version 5.7.2.
Because the vulnerability rating is critical it may mean that the consequences of not updating WordPress to version 5.7.2 may leave a site vulnerable to a hacking event.
Citation
WordPress Announcement of Version 5.7.2
Wordfence Analysis:
WordPress 5.7.2 Security Release: What You Need to Know





