GoDaddy is sending notices to customers to alert them of a hosting security breach. The security breach is described in vague terms by GoDaddy as an individual obtaining log-in information that could have given the hacker the ability to upload or change website files.
GoDaddy Hosting Compromised for Six Months
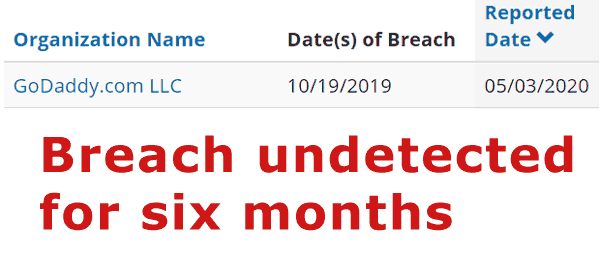
According to the California Department of Justice, the security breach occurred on October 19, 2019 and was reported about six months later on May 3, 2020.
 Screenshot from the State of California Department of Justice web page for security breach announcements.
Screenshot from the State of California Department of Justice web page for security breach announcements.SSH Access Breach
SSH is known as Secure Shell. It’s a secure protocol used to execute commands on a server as well for uploading and changing files.
If an attacker has SSH access to a website, the website is compromised.
In general, only admin level users should have SSH access because of the wide ranging changes that can be made to the core files of a website.
GoDaddy announced that an unknown attacker had compromised some of their servers.
Official GoDaddy email statement:
“The investigation found that an unauthorized individual had access to your login information used to connect to SSH on your hosting account.”
How Was SSH Compromised?
According to GoDaddy, the compromise in SSH began in October 2019 and was discovered in April 2020.
Beyond the general statement of when the breach happened and that it had something to do with SSH, GoDaddy does not appear to have disclosed any further information.
- GoDaddy does not say if this is a new vulnerability.
- GoDaddy did not say if it was from a known vulnerability from October 2019 that had gone unpatched.
The only thing GoDaddy admitted was that servers were compromised by a third party on October 2019 and it went undetected for six months.
October SSH Vulnerability
A search for SSH vulnerabilities shows that a severe vulnerability was discovered in OpenSSH 7.7 through 7.9 and all version of OpenSSH 8 up to 8.1.
The vulnerability in OpenSSH was fixed 10/09/2019 in version 8.1. That date coincides with the October 2019 date that GoDaddy confirmed as the date when their hosting servers were compromised.
GoDaddy has not confirmed if the above is the vulnerability.
The report is filed at the United States Government National Vulnerability Database report CVE-2019-16905
But the vulnerability was discovered and described by SecuriTeam where they have a full disclosure.
This is the SecuriTeam description:
“If an attacker generates a state where ‘aadlen’ + ‘encrypted_len’ is bigger than INT_MAX, then it is possible to successfully pass verification…
Any OpenSSH functionality which can parse private XMSS key is vulnerable.”
If the above is the SSH vulnerability affecting GoDaddy, which GoDaddy says began on October 2019, then that may mean whoever was in charge of maintaining the GoDaddy servers failed to update the vulnerability and the servers went unpatched until April 2020.
But we have no way of knowing for sure what happened. GoDaddy did not describe why the security breach went undetected for six months.
GoDaddy Omits Details of Exploit
GoDaddy did not say what the vulnerability was. GoDaddy did not say if this is a new vulnerability or if it is the one from October 2019 described above.
GoDaddy did not indicate whether any sites have had their files changed.
According to a report in Threatpost, this security breach affected 28,000 hosting accounts.
GoDaddy Resets Passwords
GoDaddy sent an email to affected customers to let them know that their passwords have been changed. The email has a link to the procedures to follow in order to reset the password.
How Many GoDaddy Hosted Sites Hacked?
GoDaddy did not indicate if any websites were hacked. The email sent to customers said that GoDaddy had detected “suspicious activity” on their customers servers.
According to GoDaddy:
“The investigation found that an unauthorized individual had access to your login information used to connect to SSH on your hosting account.
We have no evidence that any files were added or modified on your account. The unauthorized individual has been blocked from our systems, and we continue to investigate potential impact across our environment.”
How Did Hackers Gain Access?
GoDaddy gave no information on how the hackers obtained access to SSH login credentials. However GoDaddy did send an email to compromised customers notifying them that their passwords have been reset.
Citation
Read GoDaddy Email to affected customers, filed with the California Department of Justice
PDF Document can be downloaded from the California Department of Justice: SSH Email for Customers




