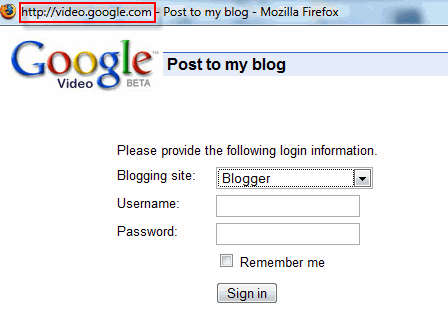
Google Video may be exposing the username and passwords of users who post videos to their MySpace accounts and serving this information over unsecure Internet protocol, with an http URL and not https.
A Google user experienced the security flaw after viewing a video on Google Video and clicking the ‘Email – Blog – Post to Myspace’ option.
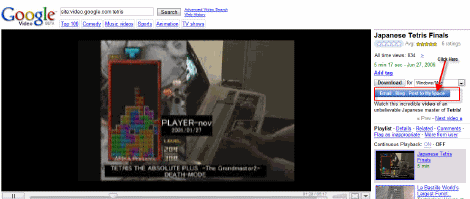
Example, go to this Google Video of the Japanese Master of Tetris playing in the 2001 Tetris Championship.
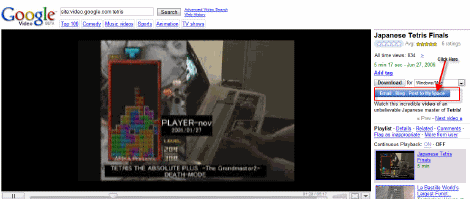
Then click ‘Email – Blog – Post to Myspace’
You will then be served this unsecure form which asks for private login information:
The user posted his experience with this on DigitalPoint forums:
So after clicking I was greeted with the following popup http://video.google.co.uk/blogpost?d…22&siteindex=3 and immediately noticed that the url of it was http, and not https. An insecure form… So I figured it must be posting the login details to a https url, so I pulled out live headers and this is what I got:
http://video.google.co.uk/blogpost
POST /blogpost HTTP/1.1
Host: video.google.co.uk
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.8.1.3) Gecko/20070309 Firefox/2.0.0.3
Accept: text/xml,application/xml,application/xhtml+xml,text/html;q=0.9,text/plain;q=0.8,image/png,*/*;q=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 300
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Referer: http://video.google.co.uk/blogpost?d…22&siteindex=3
Content-Length: 42
Cookie: PREF=ID=26c938172fc51030:TM=1178041215:LM=1138046118:S=Bw_pBCzx-opEyR3s; sloc=en_GB
Pragma: no-cache
Cache-Control: no-cache
req=login&name=myusername&pass=mypassword&site=MySpace
In a nutshell, according to this user, Google is passing private information which includes MySpace, LiveJournal, Blogger, and TypePad login details over unsecure channels. And since Blogger accounts sometimes use Google Accounts for login, such a flaw could expose a user’s GMail, Google AdWords, Google AdSense, and maybe even Google Checkout information (unless this information is encrypted).